By Dr. Jackie DAMRAU | STC Fellow
Careers for some may span a single industry or go across multiple industries. The days of working for the same employer from early age to retirement age is no longer the norm (it’s almost unheard of). Yet, as technical communicators, we know that the breadth of our field leads us in many directions.
My Cybersecurity Sojourn
My career started as a legal secretary followed by careers as a word processor, technical editor, instructional designer/trainer, business systems analyst, business process management analyst, with my next to last role being in cybersecurity.
In this article, I will share with you my 1–1/2-year cybersecurity sojourn as a Senior Risk Analyst/Senior Project Manager. I transitioned from a Senior Business Systems Analyst working on business process automation projects. This was fun, yet I accepted a challenge to transition to the Cybersecurity Governance, Risk, and Compliance (GRC) team. I knew nothing about cybersecurity at the time.
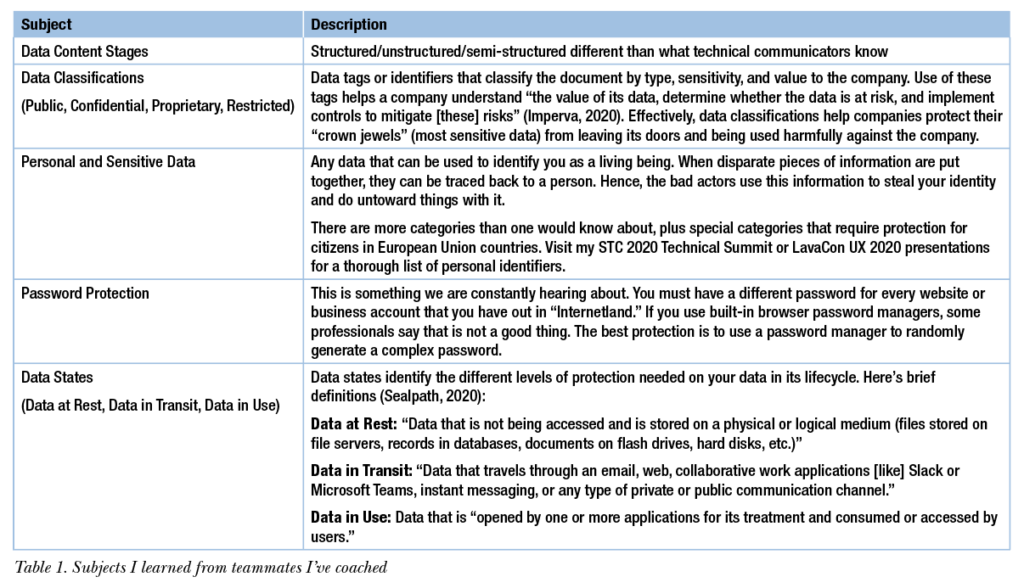
In my newly acquired role, I quickly put all my technical communication skills and experiences to practice. Soon I became the quality control point for all documentation leaving the team. I coached teammates on effective presentation skills, effective writing, and other basic skills we possess.
However, I learned from the folks that I was teaching about the subjects listed in Table 1.

My role also exposed me to international regulations like the General Data Privacy Regulation (GDPR) and the California Consumer Protection Act (CCPA). I learned that countries like Germany and France have Works Councils that require communications be passed through them for acceptance before rolling out to the employees. Even corporate policies that were of a global nature had to be presented and approved by the Works Councils; if not approved, then a separate policy had to be provided specifically for that country.
What’s Needed for a Cybersecurity Career?
A technical communicator is not “just” a writer. We are editors, graphic designers, webmasters, business analysts, social media strategists, content strategists, instructional designers, procedure writers, and much more. According to RSI Security (2020), “A cybersecurity technical writer, or information security technical writer, creates written content for an organization in partial fulfillment of a comprehensive cybersecurity strategy.…The Bureau of Labor Statistics projects that demand for technical writers [in cybersecurity] will grow by 8 percent over the next several years.” This means a new door is opening for technical communicators.
One can do a Google search for positions in cybersecurity and find that technical communicators are great candidates for these roles. Here’s just a few to that you might consider looking into (SimplyHired, 2020):
- Cybersecurity Technical Writer
- Information Assurance Technical Writer
- Information Security Analyst / Technical Writer
- Policy/Procedure/Proposal Writers – Cybersecurity
- Security Analyst / Technical Writer
- Security Consultant Technical Writer
- Skills or qualities one needs include:
- Write documentation for a specific purpose and specific audience on topics like “security policy, legal code, audit journaling, penetration test results, and business plans”
- Detail-oriented to spot high-level trends and significant anomalies with logical flow evidenced in the writing style
- Comprehension of technical concepts by learning “industry terms, understand[ing] causal relationships, and … distinguish[ing] relevant from irrelevant data”
- Determine how much jargon or industry-specific terms to use
- Play an active role as a project manager or quality assurance person for team documentation
- Willingness to continuously learn new things (the cybersecurity field constantly changes and requires knowing how to figure it out and move forward)
From roles, we move to certifications. It seems that almost every profession/career out there has some form of sanctioned certification body that adds acronyms after your name. Some of the more common ones in cybersecurity that technical communicators might consider are:
- Certified Information Systems Security Professional (CISSP)
- Certified Information Security Manager (CISM)
- NIST Cybersecurity Framework (NCSF)
- Certified ISO 27001 ISMS Foundations/Lead Implementer/Lead Auditor
- Certified GDPR Practitioner
Cybersecurity is a new area for technical communication professionals to consider. There’s lots of growth potential in this field.
Conclusion
The world of cybersecurity will open your eyes to things you may not have paid much attention to before. It did for me. I’ve given you a brief look into the world that I embraced, what skills/knowledge you need to be successful, and potential certifications/education you might consider. Enjoy your journey; reach out and let me know if you find it as exciting as I did.
Unfortunately, my company eliminated my position as a Senior Project Manager in November 2020. I was happy for the opportunity to learn a new industry and explore the opportunities that it gave me. I’m equally excited now to venture into my next role as a senior business analyst in the pharmaceuticals industry, another first for me.

JACKIE DAMRAU (jdamrau3@gmail.com) is a Fellow of STC and the Book Review Editor of the Technical Communication journal. She is a senior business analyst with Carrollton Enterprise Services in New Orleans, Louisiana. Her former role was as a senior risk analyst/project manager for CBRE, Inc.
References
Damrau, Jackie. 2020. “Structured and Unstructured Content: Perspectives from a Data Governance/Privacy Analyst.” STC Technical Communication Summit 2020.
Damrau, Jackie. 2020. “Structured/Unstructured Content from a Data Protection View.” LavaCon UX 2020.
Imperva. n.d. “Data Classification.” Accessed 17 November 2020. https://www.imperva.com/learn/data-security/data-classification/.
RSI Security 2020. “What Makes a Great Cybersecurity Technical Writer?” Accessed 22 May 2021. https://blog.rsisecurity.com/what-makes-a-great-cybersecurity-technical-writer/.
Sealpath. 2020. “Protecting the three states of data.” Accessed 22 May 2021. https://www.sealpath.com/protecting-the-three-states-of-data/.
SimplyHired. 2020. “20 Best Cyber Security Technical Writer Jobs (Hiring Now!)” Accessed 22 May 2021. https://www.simplyhired.com/search?q=cyber+security+technical+writer&job=MFptGYiTwS5vyrrVTZoWhL-ar19xaEEnxicEqxtjOXOU6wpPETT3Ng.


