By Dawnell Claessen | STC Senior Member
Technical communicators looking to expand their area of practice into cybersecurity should consider frameworks as a pathway that will have many familiar skill sets, work products, and methods. In technical communication (TC) we are well accustomed to establishing and adhering to guidelines and standards, so conducting our work inside a frame of reference (like a framework) should be an easy and logical career step.
What Is a Framework, Anyway?
A framework is a tailored set of standards and rules that can be used to form a persistent and reusable infrastructure that organizations use to conduct operations. Frameworks can be as rigid or flexible as an organization needs and are used to execute strategy and meet goals and objectives. Frameworks are also commonly used to assess or demonstrate compliance with specific regulations.
Frameworks are a versatile tool and can be applied as a business model that could be used for research and development of just about anything imaginable. Coding and programming are most often done using a framework of some sort for consistency. Because frameworks allow for a consistent process execution, they can make repeatable processes easier and make both compliance assessment and demonstration more successful. Increasingly, businesses and organizations are relying on frameworks for cybersecurity and TC to fulfill a large and vital part in their use.
A security framework is the system of security specific guidelines, policies, regulations, and standards an organization adheres to in achieving its security objectives. This may include physical security, personnel security, as well as security of information, systems, and intellectual property.
A cybersecurity framework then is the set of core functions that an organization specifically identifies and performs concurrently and continuously according to set guidelines and standards to achieve its cybersecurity objectives. Often those objectives include things like risk management and/or compliance with regulation.

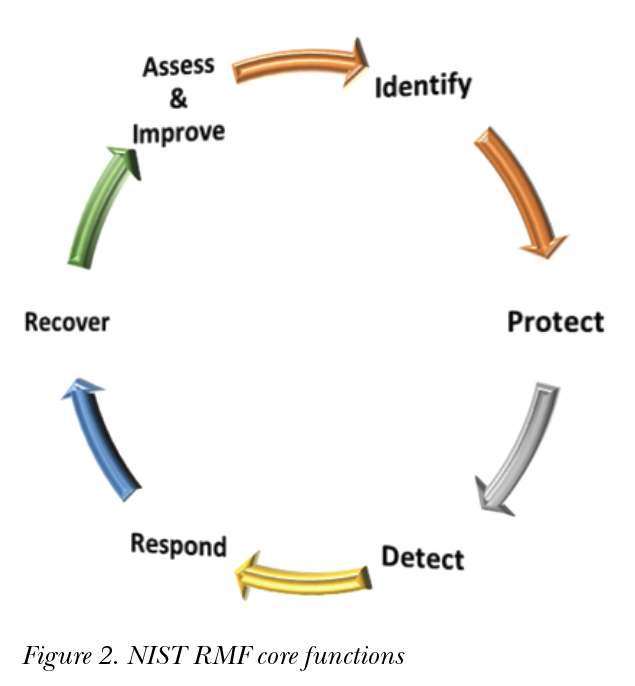
Dozens of cybersecurity frameworks are in use worldwide. One of the most common cybersecurity frameworks in the United States (U.S.) is the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF). The NIST RMF has components, tiers, attributes, and functions. The core functions of this framework are: Identify, Protect, Detect, Respond and Recover (Figure 2). Each core function of most cybersecurity frameworks has a set of controls, including the NIST framework. Each control has implementation guidance and assessment procedures.
ISO IEC 27001/ISO 27002 and the ISO 27001 cybersecurity frameworks contain international standards with both having recommendations on a set of requirements and controls. The General Data Protection Regulation (GDPR) is common in Europe, including many industry-specific frameworks like health care, payment cards, manufacturing, etc. Most U.S. frameworks are voluntary, but international frameworks are linked even more closely to compliance with regulations and standards. In other parts of the world, the use of frameworks may be a requirement for certain business types like in Europe with businesses in the payment banking and finance areas.
All frameworks can be tailored and should be used to assess adherence to standards and to improve upon the processes it contains. Choosing an established cybersecurity framework for your organization provides many advantages, like pre-written requirements, taxonomies, standard artifacts, and even templates to make getting started easier.
Cybersecurity Capability Maturity Model (C2M2)
The C2M2 is a maturity model that organizations can use to measure the maturity of their cybersecurity capabilities. This is typically implemented when an organization wishes to demonstrate or prove that their cybersecurity processes are performed at a certain level of maturity. For example, some contracts that have cybersecurity responsibilities require that bidders be performing at a certain level to even be considered.
There are 10 domains in the model (which is also considered a framework) and each domain has practices and at least three maturity levels. Often these practices are related to management functions, such as risk management, identity and access management, configuration management, supply chain management, and other specific cybersecurity objectives.
Opportunities for Technical Communicators
Technical Communicators are excellent candidates for a career in cybersecurity and especially for working with frameworks. We already know our audience and we know a lot about our organization’s people, products, and processes. And we excel at using technology to create and share our knowledge and skills. Automation tools as well play key roles in frameworks. TCs can synthesize all these elements into content that is readable and supports cybersecurity efforts.
Frameworks often come with built-in templates that can be implemented immediately and serve as starting points for developing a library of required process documents. Business processes within your own organization are likely to be linked to a framework of some sort, and they are an accessible and excellent way to get involved with frameworks.
The Art of Artifact Creation and Maintenance
Compliance to a framework of standards and guidelines and their associated policies and procedures is / should be “artifact-centric” by design. TCs are (or can quickly become) experts at “compliance by design” with an artifact-centric approach to writing. All that means is that inception processes are modeled and procedures are written in a more declarative manner (with the goal of compliance and artifacts) versus the imperative (a sequence of steps and actions). This style of writing is what we as TCs would have little trouble implementing.
Artifacts should be a natural work product of any framework. This is the area where TCs can really bring value to the team. As with any form of compliance, an organization must always “say what we do” (follow the process), “do what we say” (generate quality artifacts and records), and “prove it and improve it” (assess, audit, and act on discrepancies).
Many cybersecurity frameworks come with a set of standard artifacts and deliverables that typically start with a security plan that addresses all requirements, at least at a high level. Often there are plans subordinate to the main security plan. There are also process documents, requirements and controls, as well as formal reports, lots of metrics to track, and presentations that also present opportunities for TCs to show off their skills.
Getting Started
The news is filled with reports of unfilled cybersecurity jobs—Forbes magazine and Cybersecurity Ventures estimate as many as 3.5 million jobs globally by the end of 2021. So, the opportunities exist, and not just for those with hard technical skills and computer science degrees. Frameworks especially rely on communication—good planning and good documentation that is available and accessible to everyone in the organization. Good communication skills are always expected to round out a skill set and should always be highlighted on a résumé. Project management skills are also in remarkably high demand in cybersecurity and framework positions.
There are several ways to get started. First, determine if cybersecurity and frameworks is a good fit for your skill set and career goals. If you think it is, be flexible and know you can always grow your skill set—“upskilling” and “reskilling” is common in cybersecurity so you will constantly be sharpening your non-technical communication skill set. Frameworks are constantly evolving and maturing to match regulations and standards. The ability to learn new things—new technology, new regulations, and standards, all the while using a basic skill will be key to success in cybersecurity.
You can also find opportunities by simply browsing the many job postings online that contain the words cybersecurity + frameworks. Look at the job descriptions and skills noted in the posting and consider what interests you. Writing or technical communication may not be mentioned, so look for terms like policy, process, procedures, assessment, compliance, reports, and artifacts. Look within your company for areas in your current organization that have openings or just need your help. That can be as a job seeker, a consultant, or within your current organization. You can also work with online recruiters and temporary placement agencies. And you can always just decide to go for it! Then, make a career transition plan and do whatever it takes to set yourself up to succeed.
Tools and Techniques
Frameworks are often implemented through technology. The key to success is being able to use these tools. For example, process tools which enforce an automated compliant workflow. Power Automate and SharePoint are very commonly used, but there are many others. Skills with word processing and spreadsheets is an absolute must. Again, our good communication skills come in handy. The use of presentation software and good speaking and presenting skills are always valued.
After communications skills, being able to quickly adapt, to pick up and use new tools and techniques will always serve TCs well and set us apart in the cybersecurity field.
Role of Certifications
In technical communication and cybersecurity, a certification demonstrates a certain level of competency as well as a commitment to the field of practice. This is especially true in cybersecurity where they are quite common. A certification can open doors in cybersecurity and frameworks and lead to advancement opportunities. If there is a certification that is common in your industry or at your workplace, preparing for a new certification is a way to signal interest and get noticed. Many jobs require or strongly prefer a four-year college degree. But for those who have not completed a bachelor’s degree, one or more certifications can help with getting started and advancing in cybersecurity and frameworks.

There are many certifications to consider but one option is to first obtain a Certified Professional Technical Communicator (CPTC) certification and then add a hard skills certification and possibly a project management certification. A certification that is specific to an industry is likely to be extremely helpful in that field but does limit your options a bit.
Consider a certification in a “hard-skill” and choose one you already know, or one that is in demand and technology specific, such as Cisco for computer networking, VMWare for virtualization, Microsoft for Systems Administration, Amazon Cloud, and many others. Spend time browsing job postings and job descriptions of positions and make notes of which ones are mentioned the most. Then consider those that are the best fit for you.
There are many certifications to consider. Here is a list of a few well-known certifications—a quick search online should yield details about each one.
- STC’s Certified Professional Technical Communicator (CPTC)
- Information Technology Infrastructure Library (ITIL): Numerous certification offerings with levels of advancement and many specific to process. Very desirable with levels of advancement.
- OCEG’s Governance Risk and Compliance Professional (GRCP) and GRCA (Audit)
- PMI’s Project Management Professional (PMP)
- CompTIA: Multiple cybersecurity and technical certifications along a career advancement path
- ISACA’s Certified Information Systems Auditor
- ISC(2): CISSP and others
Conclusion
Cybersecurity and frameworks present opportunities for technical communicators willing to adapt and stretch their skill sets and to not be too focused on job titles. Cybersecurity is a well-paying career field that values and welcomes a varied skill set. Communication skills, technical skills, management skills, and software and systems skills at almost any level are highly used. Don’t be afraid to speak up and apply for that job or express your interest in cybersecurity. Sharpen your technical skills and pursue a certification in something that interests you. Volunteer or offer to help on a project related to cybersecurity and frameworks. Many companies (including mine) offer “transition plans” for people looking to move into cybersecurity for other fields. Good luck! gi

DAWNELL CLAESSEN (mail@dawnell.com) is a technical communicator and certified security systems professional (CISSP) specializing in security certification and accreditations of information systems operated by the Defense Health Agency and Veterans Health Administration. She works constantly with the NIST Risk Management Framework and the Cybersecurity Maturity Model. Dawnell holds a Master of Library and Information Science with a specialization in federal information policy from the University of Texas at Austin. For STC, Dawnell also acts as a co-manager of the Policies and Procedures Community and she is really hoping that this article will win her brownie points (and a polo shirt) with the Florida Chapter of STC’s Active Member Program.
References
NIST RMF Framework. “New to Framework.” Accessed 21 May 2021. www.nist.gov/cyberframework/new-framework.
Sayegh, Emil. “As the End of 2020 Approaches, the Cybersecurity Talent Drought gets Worse.” Forbes. Accessed 21 May 2021. www.forbes.com/sites/emilsayegh/2020/09/22/as-the-end-of-2020-approaches-the-cybersecurity-talent-drought-gets-worse/.
The Missing Report. “Cybersecurity Frameworks 101 – The Complete Guide.” Accessed 21 May 2021. www.preyproject.com/blog/en/cybersecurity-frameworks-101/.
Toolshero. “Communication Strategy Framework.” Accessed 21 May 2021. www.toolshero.com/communication-skills/communication-strategy-framework/.


